Node SDK
Getting started
You can find the official SDK page here which explains how to install and initialise the client.
Creating travel rule messages
There are three ways to create and send a travel rule messages using the SDK:
- Basic transaction - Hosted
- End-to-end encryption
- Hybrid encryption
See here for more information about the encryption.
Hosted Encryption
Notabene encrypts all raw Travel Rule transaction data created through our easy-to-use restful API without worrying about local key management. Each VASP has a dedicated encryption key managed by Notabene’s PII service and can be rotated on-demand.
const { Notabene } = require("@notabene/nodejs");
const client = new Notabene({
authURL: 'https://auth.notabene.id',
baseURL: "https://api.notabene.dev",
audience: "https://api.notabene.dev",
clientId: "xxxxxxxxxxxxxxxx",
clientSecret:"xxxxxxxx-xxxxxxxxx",
baseURLPII: "https://pii.notabene.dev",
audiencePII: "https://pii.notabene.dev",
});
const ivms = {
originator: {
originatorPersons: [
{
naturalPerson: {
name: [
{
nameIdentifier: [
{
primaryIdentifier: 'Normann',
secondaryIdentifier: 'Christoffer'
},
],
},
],
geographicAddress: [
{
addressLine: ['Oslo street 123, 2001, Oslo'],
country: 'NO'
},
],
},
},
],
accountNumber: ['01234567890'],
},
beneficiary: {
beneficiaryPersons: [
{
naturalPerson: {
name: [
{
nameIdentifier: [
{
primaryIdentifier: 'Danskmann',
secondaryIdentifier: 'Niels'
},
],
},
],
},
},
],
accountNumber: ['01234567890'],
},
};
const payload = {
transactionAsset: 'BTC',
transactionAmount: '123456789',
originatorVASPdid: 'did:ethr:0xd4bd902ec78578f33a20ff601504d2ab324cfab9',
beneficiaryVASPdid: 'did:ethr:0xb62c155177f40d3ad75d2d19c087fcc69a1be7a0',
transactionBlockchainInfo: {
origin: '0x12htre3456337897grt5644e56dtv',
destination: '0x3215867fff456brt342436423',
},
originator: ivms.originator,
beneficiary: ivms.beneficiary,
};
const myfunc = async function(){
const txCreated = await client.transaction.create(payload);
console.log(txCreated);
}
myfunc().catch((err)=>console.error(err));
End-2-End Encrypted
End-to-End Escrow PII brings the most security, as the Originating VASP encrypts PII data so that only they and the Beneficiary VASP can decrypt it:
const { Notabene } = require("@notabene/nodejs");
const client = new Notabene({
// same as above
});
const ivms = {
// same as above
};
const payload = {
// same as above
};
const jsonDIDKey = '{"did": "did:key:z6MkjwpTikNZkpfop2ebcbPfsxi786ftTr9nGBD3XKKHZ2S", "keys": [{"privateKeyHex": "0d07d8acda928f98765e4a0b80013e2be369c29564419ac3ba08107599aeb3fc519b59a6b7ebf128f6c6af4081f5e512750e1b4e47f08263dbc656b7b3541c33"}]}';
const myfunc = async function(){
const txCreated = await client.transaction.create(
payload,
jsonDIDKey);
console.log(txCreated);
}
myfunc().catch((err)=>console.error(err));
Notabene dashboard + E2E
You will not be able to see the details within the Notabene dashboard when using E2E encryption.
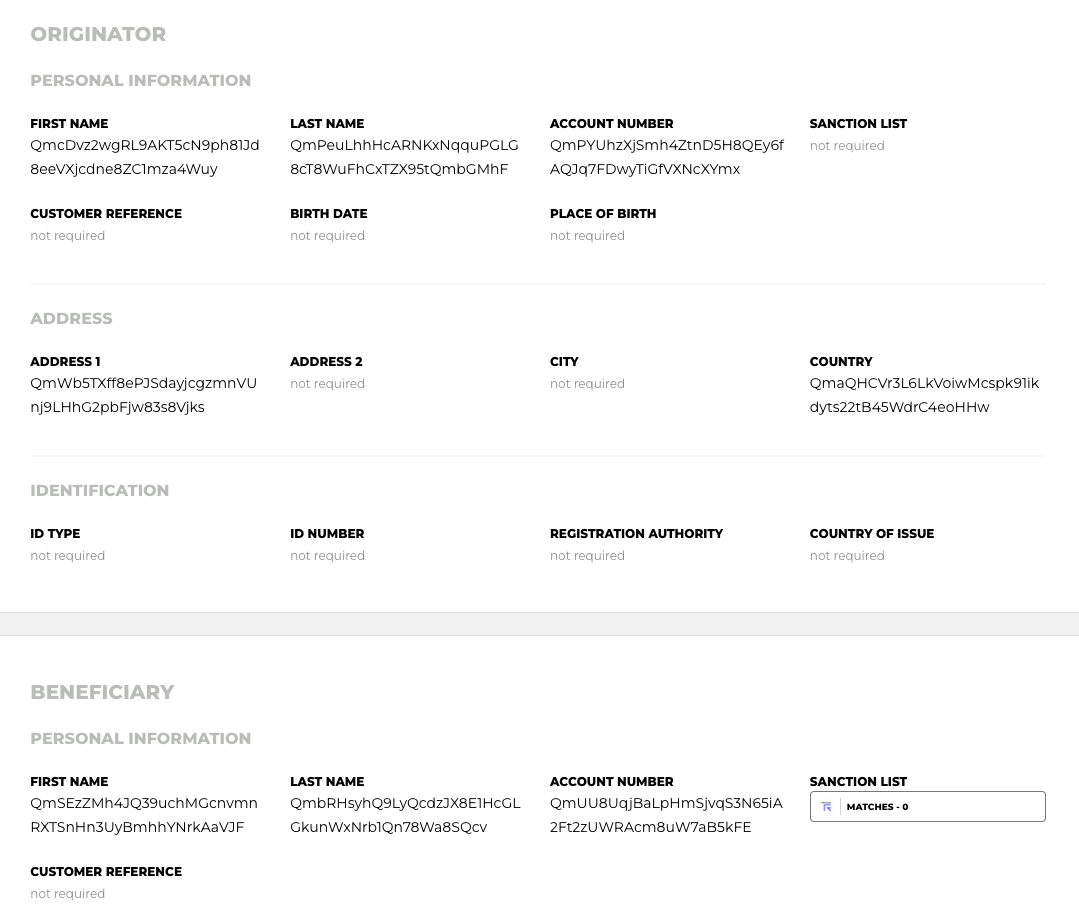
Hybrid Encryption
The Hybrid Escrow PII mode extends the End-to-End flow, where the Originator VASP further encrypts the PII data selectively using their dedicated Notabene-managed encryption key, allowing Notabene to decrypt the PII (or parts of the PII data) for in-flow pre-transaction name sanction screening:
const { Notabene } = require("@notabene/nodejs");
const client = new Notabene({
// same as above
});
const ivms = {
// same as above
};
const payload = {
// same as above
};
const jsonDIDKey = '{"did": "did:key:z6MkjwpTikNZkpfop2ebcbPfsxi786ftTr9nGBD3XKKHZ2S", "keys": [{"privateKeyHex": "0d07d8acda928f98765e4a0b80013e2be369c29564419ac3ba08107599aeb3fc519b59a6b7ebf128f6c6af4081f5e512750e1b4e47f08263dbc656b7b3541c33"}]}';
const myfunc = async function(){
const txCreated = await client.transaction.create(payload,jsonDIDKey,true);
console.log(txCreated);
}
myfunc().catch((err)=>console.error(err));
Notabene dashboard + Hybrid
With this flow, you can decrypt and view the data within the Notabene dashboard.
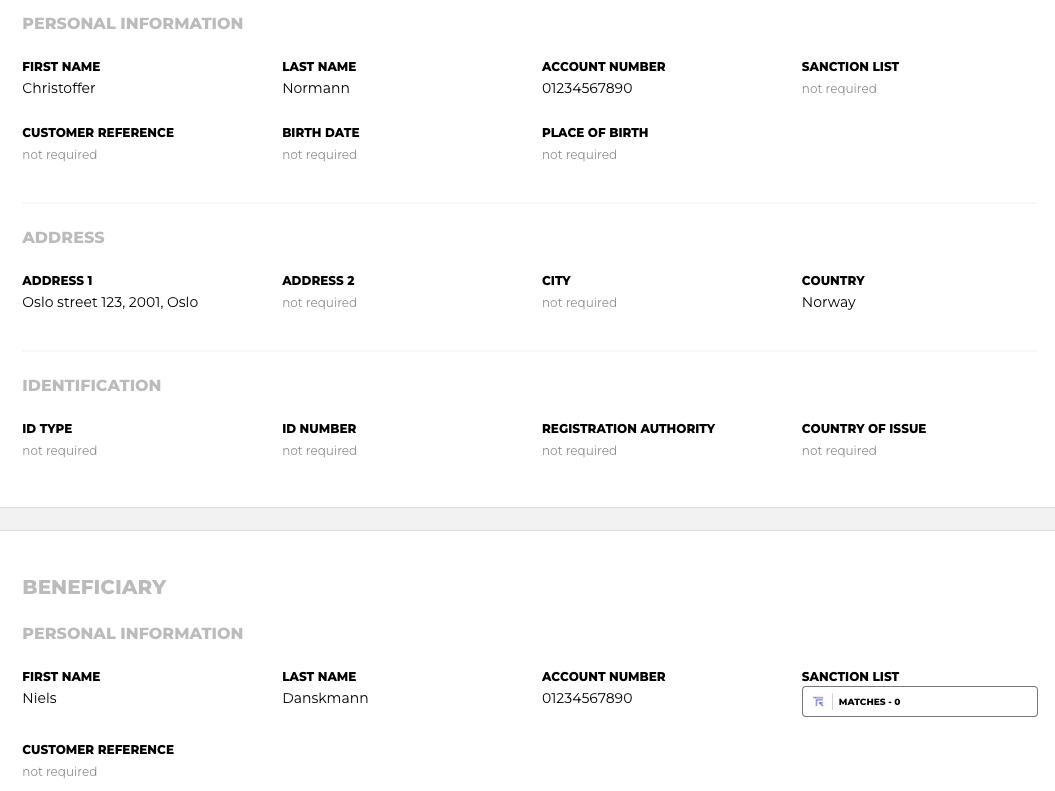
Creating your JsonDIDKey
For End-2-End and Hybrid encryption, your VASP needs a dedicated DIDKey which is a public-private keypair. You can create a new keypair using the @notabene/cli and then publish it to the Notabene directory under the pii_didkey field. This allows other VASPs retrieve your public key and encrypt PII data to you.
Please see the guide here.
Other important methods
Validate travel rule content
Pending.
const txValidateFull = await client.transaction.validatefull({
transactionAsset: ETH,
transactionAmount: 1700000000000000000,
originatorVASPdid: {{vaspDID}},
originatorEqualsBeneficiary: false,
validatePartyFields: BENEFICIARY,
transactionBlockchainInfo: {
origin: 0x1483C7594CF06Bc5cA551c790F0E3ba6f8416F4b,
destination: 0xdAC17F958D2ee523a2206206994597C13D831ec7
}
});
redirect transaction
client.transaction.redirect(fromDID, toDID)
const txRedirect = await client.transaction.redirect({
fromDID: vaspDID,
toDID: vaspDID2
});
Redirecting transaction allows gateway VASPs to route incoming transactions to the correct subsidiary
check blockchain deposit against travel rule
Check if an incoming deposit has received travel rule information or not.
const myfunc = async function () {
const txNotified = await client.transaction.notify(
"thisisthehash",
"123456789",
"BTC",
"did:ethr:0xd4bd902ec78578f33a20ff601504d2ab324cfab9",
"destinationAddress",
"originAddress"
);
console.log(txNotified);
};
myfunc().catch((err) => console.error(err));
Full list
For a full list of methods you can call with the SDK, please see here.
Updated 9 months ago
